Asset Scanning


Endpoint security
Risk data is ingested from NVD, Microsoft, CISA and ExploitDB
Vulnerabilities are classified based on the CVSS and EPSS score
For MacOS, Linux, Windows
Deployment via Intune, GPO, manual
Historical insight
Each find software anywhere
Secured via API keys
Identify vulnerable assets in an organisation
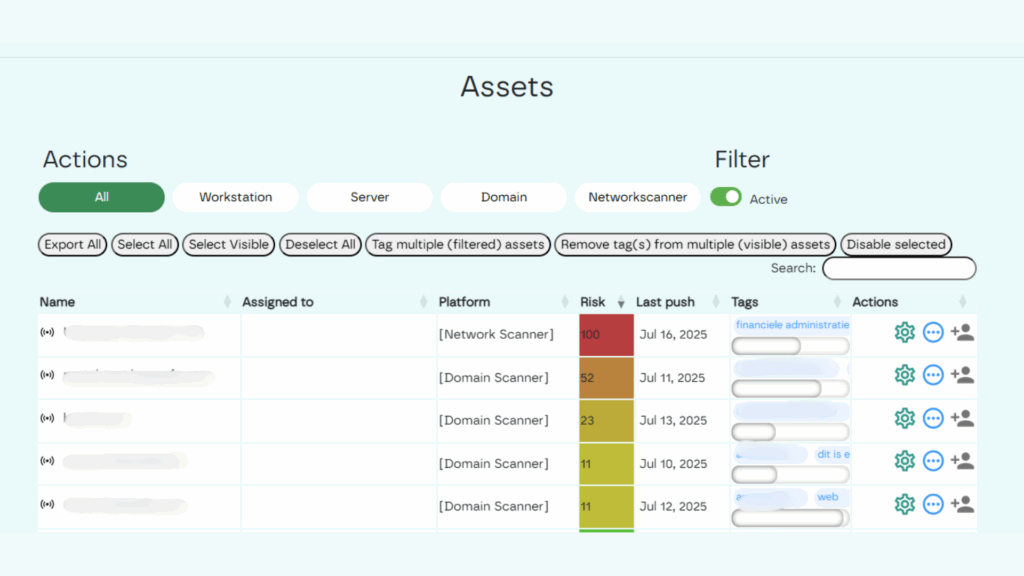
The platform performs an analysis of the software and vulnerabilities on MacOS, Linux, Windows and the presence of basic weak policies and patches on computers running Windows.
Data
External risk data is ingested from NVD, Microsoft, CISA and ExploitDB. The portal stores and shows all end points, ports & services, software & versions of the network segments. Software vulnerabilities are classified based on the CVSS score and the EPSS score. Historical data is stored to make comparisons possible. Vulnerabilities are mentioned according to CVS. For each host settings and asset prioritisation can be set, asset tagging and warning level can be applied.
Results
Users are alerted directly when vulnerabilities are found. All findings can be reviewed in the Power BI dashboard and shared with others. The detailed information is available on the portal.
For more scanning services, our domain scanning delivers similarly comprehensive results.
Regulation
No PII data is collected but users can decide to link assets to employees. This is pending agreements between employer and employee. The data can show who is using what software or apps.
Endpoint connection for all APIs, Windows, policies, patches
Risks reports scores as CVSS and EPSS
Risk assessment of both rapid rivew and comprehensive analysis
No Credit Card Required
Get cyber security & training automated