Network Vulnerability Scanning
Core Features
Network Scanning
Regular scanning of all hosts and services
Multi segment
Vulnerability summary and monitor
Enhanced Identification e.g. MySQL, RDP, and unencrypted ports
Historical Network Activity
Secured via API keys


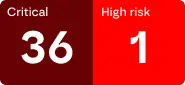

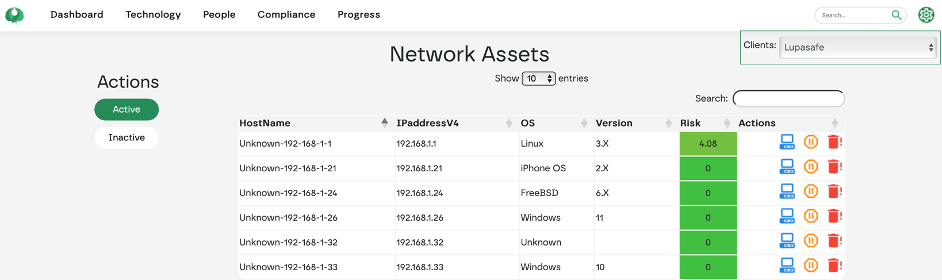
Continuous, frequent scanning of internal network segments for hosts and services identifies vulnerabilities.
Data
External risk data is ingested from NVD, Microsoft and CISA. The portal stores and shows all hosts, ports & services, software & versions of the network segments. Software vulnerabilities are classified based on the CVSS score and the EPSS score. Historical data is stored to make comparisons possible. Vulnerabilities are mentioned according to CVS. For each host settings and asset prioritisation can be set, asset tagging and warning level can be applied.
Results
As soon as vulnerabilities are identified, users receive alerts based on their settings. All findings can be reviewed in the Power BI dashboard and shared with others. Detailed information is available on the portal and in reports. Our domain scanning services can provide equally comprehensive results.
Continuous nmap scans
Finger printing of software and versions
Data used for compliance and prioritised for dashboard
No Credit Card Required
Awareness Training
& Security Assessments